Resource Library
Join the Webinar
Explore the future of AI infrastructure:
- RAC architecture for autonomous, scalable AI systems
- Self-optimizing ecosystems powered by intelligent agents
- ✓ Proven frameworks to align AI with dynamic business goals
Location:
Online
18
March
2026
2026
Time:
8:00 AM EST
30 Minutes
Brochures

BROCHURE
vSOCBox CASB
A Single Security Solution for Multiple cloud applications and integration.
BROCHURE
vSOCBox SIEM (Product Guide)
Flexible integration to Augment Your Security Stack AI/ML based SIEM (UEBA+XDR+SOAR).
BROCHURE
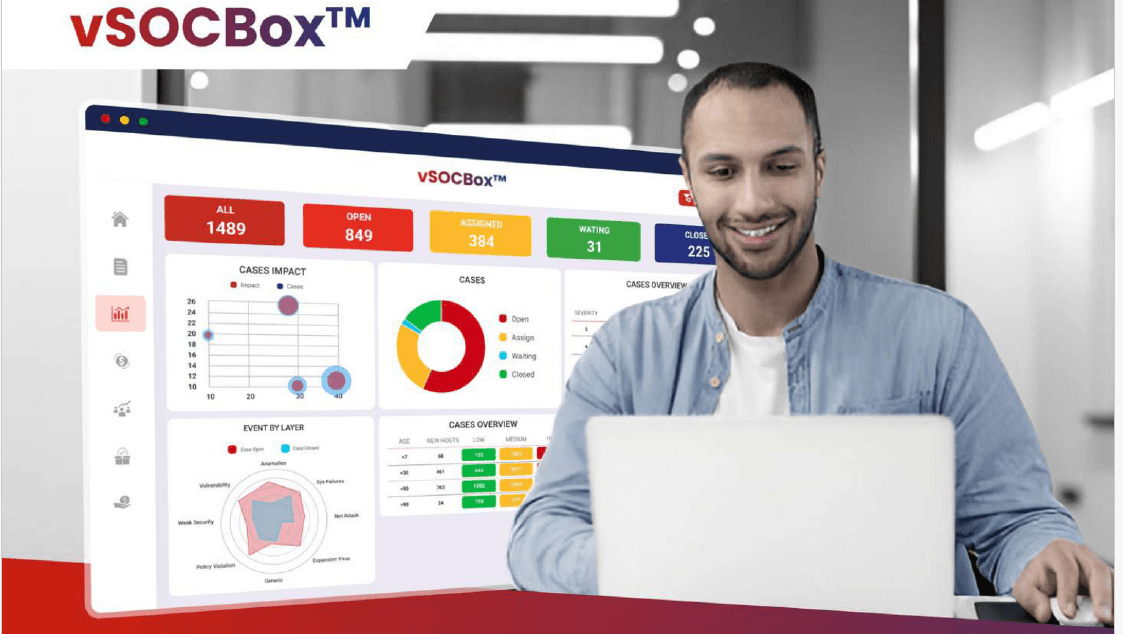
About vSOCBox
An all-in-one SOC-in-a-Box solution delivering comprehensive security, intelligent automation, and real-time threat detection.
BROCHURE
AIML powered
A unified, MI/ MI- dowered SOC in a Box delivers smart, real-time threat detection and remediation.

BROCHURE
vSOCBox AI-Powered Cybersecurity Solution Sales Battle Card
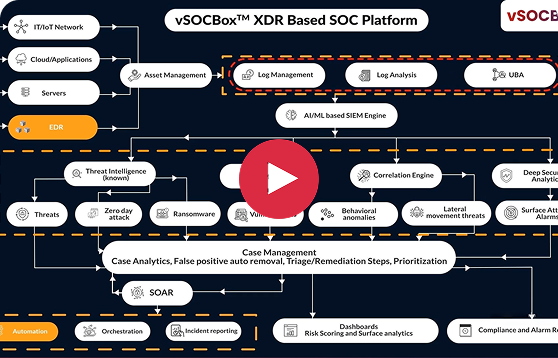
vSOCBoxTM AI-powered platform revolutionizes security management by leveraging AI and Machine Learning for superior threat detection and efficient event correlation. This advanced system not only automates security monitoring but also accelerates threat identification and also ensures real-time alerting, allowing security teams to focus on genuine threats.

BROCHURE
SOC-in-a-Box: Unified Cybersecurity for Modern Enterprises
Discover the platform that secures and insures. Consolidate point solutions in a box. Automated Al-enabled MDR. Reduce costs. Stop the breach for all layers.
Data Sheets

DATA SHEETS
Log Management
Effectively neutralize threats and suspect behavior with proactive intelligence.

DATA SHEETS
Access Management
One system to rule them all: users, devices, things, applications, and services.

DATA SHEETS
Patch Management
Streamline and accelerate vulnerability remediation for all your IT assets.

DATA SHEETS
EDR
Malware incidents have significantly decreased since we migrated to qualys Endpoint security.

DATA SHEETS
SIEM & Log Management
vSOCBox Cloud native SIEM discover and priorities real threats in real time.

DATA SHEETS
Security Analytics
Security Analytics helps parse and enrich logs, wire data and event data from any data source.

DATA SHEETS
User & Entity Behavior Analytics
vSOCBox UEBA monitors and analyzes the behavior of user and other entities.

DATA SHEETS
Using AI for Offensive Security
vSOCBox offers an Offensive security platform that secures and ensures your enterprise security infrastructure against vulnerabilities.

DATA SHEETS
Ticket Generation Guide
In case of any issues regarding services, device onboarding, new integration client has to raise the ticket

Data Sheets
vSOCBoxTM SOAR For Firewall
Broaden Your Cyber Protection and Privacy with vSOCBox
Articles

ARTICLES
Unified Cybersecurity Platforms As A Trend For 2025
Are just in the third week of 2025 and there wouldn’t be a perfect time to remould, rethink, and restructure your cybersecurity models than now.

ARTICLES
AI and Automation: The Future of Cybersecurity is Here
Discover how AI and automation are transforming cybersecurity by enhancing threat detection, response, and resilience, helping organizations stay ahead of cyber threats.

ARTICLES
The Dangers of Siloed Security: Addressing Key Challenges
Siloed cybersecurity has its set of disadvantages. How do we address the same? As technology advances by leaps and bounces, reliance on it has also increased exponentially.

ARTICLES
Is Your Security Strategy Too Fragmented? The Risks of Multiple Solutions
Being fragmented is no more in vogue, at least in the cybersecurity scheme of things. Is your enterprise still adopting standalone solutions?

ARTICLES
Cybersecurity and the Internet of Things (IoT): Securing Your Connected Devices
Securing IoT devices is no more a “good to have practice” given their vulnerabilities; it is non-negotiable. Choosing the right software is pivotal to ensure zero security leaks and to build a resilient ecosystem.

ARTICLES
Elevating Cyber Defense: How a Unified Security Platform Accelerates Cyber Incident Responses
With technology advancing at an unprecedented rate powered by AI, newer security compromise mechanisms have cropped up. Given the scenario, a few probing questions arise.

ARTICLES
Is your SME a Cybersecurity Target?
Today’s hyper-connected business landscape is rampant with security attacks and malicious entrants. What Small and Medium Scale businesses must not do is sleep with the comfort of knowing they are not a party to cyber threats.
Case Studies

Case Studies
How One BFSI Enterprise Transformed Its Security Operations with vSOCBox
The Challenge: Drowning in Alerts, Struggling for Clarity

Case Studies
Drowning in Alerts: A Government SOC's Journey from Chaos to Control
Discover how AI and automation are transforming cybersecurity by enhancing threat detection, response, and resilience, helping organizations stay ahead of cyber threats.

Case Studies
Sterling Diagnostics
Sterling Diagnostics hit 99.99% uptime and 80% faster incident response with vSOCBox.A unified ‘SOC-in-a-Box’ delivering full cybersecurity as a service.

Case Studies
Agilus Diagnostics
Agilus Diagnostics boosted efficiency and reduced risk by automating 60% of threat responses with vSOCBox SOAR — powered by a unified ‘SOC-in-a-Box’ delivering security as a service.

Case Studies
Hiranandani Group
Hiranandani Hospitals hit 99.99% uptime with vSOCBox, shielding care and revenue from cyber threats. A single, unified ‘SOC-in-a-Box’ delivers every security service on demand.

Case Studies
Beyond Products: Top 5 C-Saas for Streamlined, Scalable Security
In a hyper-connected world powered by AI and its prowess, enterprises are prone to threats and cyberattacks at an unprecedented magnitude. To stay immune to threats and security glitches from a 360-degree perspective, one must choose some of the best ways to secure their IT infrastructure.

Case Studies
From Compliance Chaos to Cyber Confidence: The Story of a U.S. Federal Credit Union
In the heart of Mississippi, a mid-sized Federal Credit Union was expanding rapidly, but with growth came complexity. With over 200K members and assets exceeding $2.2 billion, the institution faced a whirlwind of audits — multiple times a month — by the National Credit Union Administration (NCUA) and other financial regulators.

Case Studies
Driving Enterprise-Wide Protection: How India’s Largest Car Manufacturer Secured 3,000+ Locations
Managing cybersecurity for one office is hard. Imagine managing it for 15 regional offices, 1,950 sales points, and over 3,000 service centers scattered across 1,500+ cities in India. This leading car manufacturer was losing control over its vast network of applications, endpoints, and branch infrastructure. It lacked forensic analysis tools, had no unified visibility across the landscape, and compliance with ISO 27001 and CERT-In mandates was a growing nightmare.

Case Studies
From Audit Anxiety to Always-On Security: A Top NBFC’s Journey with vSOCBox
This NBFC was growing fast and operating under the radar of strict financial compliance laws including RBI-CSF, HIPAA (due to insurance apps), and HITRUST frameworks. With over 250 branches, the company had zero in-house security staff and was failing monthly audits. Its environment included critical financial applications that handled sensitive PII and transactional data.

Case Studies
Empowering MSME Lending: How Veritas Finance Transformed Identity Governance with vSOCBox
Veritas Finance, a fast-growing NBFC supporting MSMEs, struggled with identity sprawl. Employees used both home-grown and commercial apps across 230 branches, but the organization had no centralized identity or access governance. Manual provisioning and deprovisioning processes were inefficient and error-prone, putting operational and regulatory risk on the table.

Case Studies
Securing Financial Assets: How Orbis Financial Scaled Compliance with vSOCBox
With over 36 audits annually, Orbis Financial needed to protect billions in client assets from cyber threats, identity theft, and fraud. Their challenge was not just prevention — but to prove, repeatedly, to auditors that controls were effective.

Case Studies
Scaling Secure Lending: How Magma Fincorp Mitigated Internal Threats with vSOCBox
As a financial services player with deep rural penetration, Magma Fincorp faced rising risks from internal threats and advanced attacks. Audit requirements demanded strict data leakage and access control logs, which were difficult to manage without centralized tooling.
Case Studies
Smarter Alerting & Faster Remediation: How Exide Life Insurance Optimized SOC Efficiency
Exide Life’s SOC was plagued with noise — false positives, duplicate alerts, and alert fatigue. The remediation team wasn’t staffed 24x7, leading to long delays in resolution. Manual errors during incident handling worsened the problem.

Case Studies
Operational Visibility & Control: How Keesler Credit Union Gained Control Over Compliance
With heavy NCUA oversight and 24 branches, Keesler Credit Union needed real-time visibility into geo-distributed infrastructure, including Windows/Linux systems and firewalls. Compliance documentation was manual and time-consuming.

Case Studies
vSOCBox: AI And ML Based SIEM Platform For Government Entity
vSOCBoxTM was deployed on their environment, enabling their SOC to become more intelligence-driven, by allowing them to centralize all their alarms, while aggregating & validating data from a wide variety of solutions like SIEM, UEBA, NGFW and threat intelligenceQ

Case Studies
vSOCBoxTM : AI And ML Based SIEM Platform For BFSI
vSOCBoxTM deployed for centralization of alarms with Big Data, which can be analyzed with ML to remove noise, duplication of alarms coming from different security solutions and to bring context like Assets-UsersBusiness to enrich the alarmsK
Webinar