vSOCBoxTM
Endpoint Detection & Response (EDR)
Proactive Threat Detection at Your Fingertips
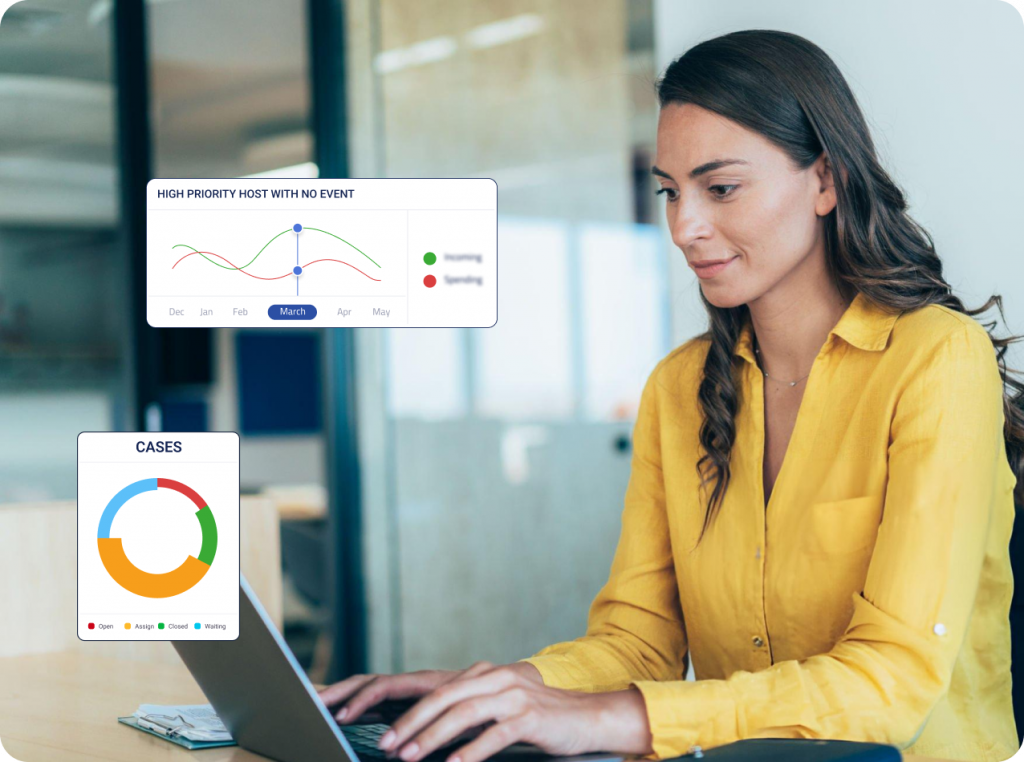
Protect Your Business. Simplify Your Security.

Real-Time Threat Mitigation

Seamless Integration

Comprehensive Protection
Why Choose
vSOCBoxTM EDR?

Real-Time Monitoring
Stay ahead of threats with 24/7 monitoring of all endpoint activities.

Automated Response
Quickly mitigate risks with automated threat response capabilities.
Customizable Policies
Tailor our in-built policies to suit your organization’s unique security needs..
Scalable Solution
Whether you’re a small business or a large enterprise, vSOCBoxTM EDR scales to meet your needs.
Key Features
Behaviora Analysis
Threat Intelligence Integration
Our EDR solution is integrated with the latest threat intelligence feeds, allowing it to recognize and respond to emerging threats as soon as they are discovered in the wild.
Automated Mitigation
Experience the Power of AI-Driven Cybersecurity.

Centralized Dashboard
vSOCBoxTM EDR features a user-friendly, centralized dashboard that displays real-time information on endpoint activities, threats, and response actions. This dashboard provides your security team with a clear overview of your organization’s security posture, enabling quick decision-making.

Deep Forensic Analysis
In the event of a security breach, vSOCBoxTM EDR’s forensic capabilities allow you to conduct a thorough investigation. Our solution provides detailed data on the attack vector, enabling your team to understand how the breach occurred and how to prevent similar incidents in the future.

Threat Hunting
With vSOCBoxTM EDR, your security team can proactively hunt for threats across your network. Our solution provides the tools necessary to search for indicators of compromise (IOCs) and uncover hidden threats that may have gone undetected by automated systems.

Application Control
vSOCBoxTM EDR includes application control features that allow you to restrict the execution of unauthorized software. This prevents malicious applications from running on your endpoints, reducing the risk of infection.

Device Control
Control the use of external devices, such as USB drives, with vSOCBoxTM EDR’s device control capabilities. This feature helps prevent data exfiltration and the introduction of malware through removable media.

Patch Management
Keeping your software up to date is critical for security. vSOCBoxTM EDR integrates with your patch management processes, ensuring that your endpoints are always protected against known vulnerabilities.

Detect, respond, and prevent threats in real time, ensuring the protection of your critical data and systems.
TRUSTED BY LEADING ORGANIZATION