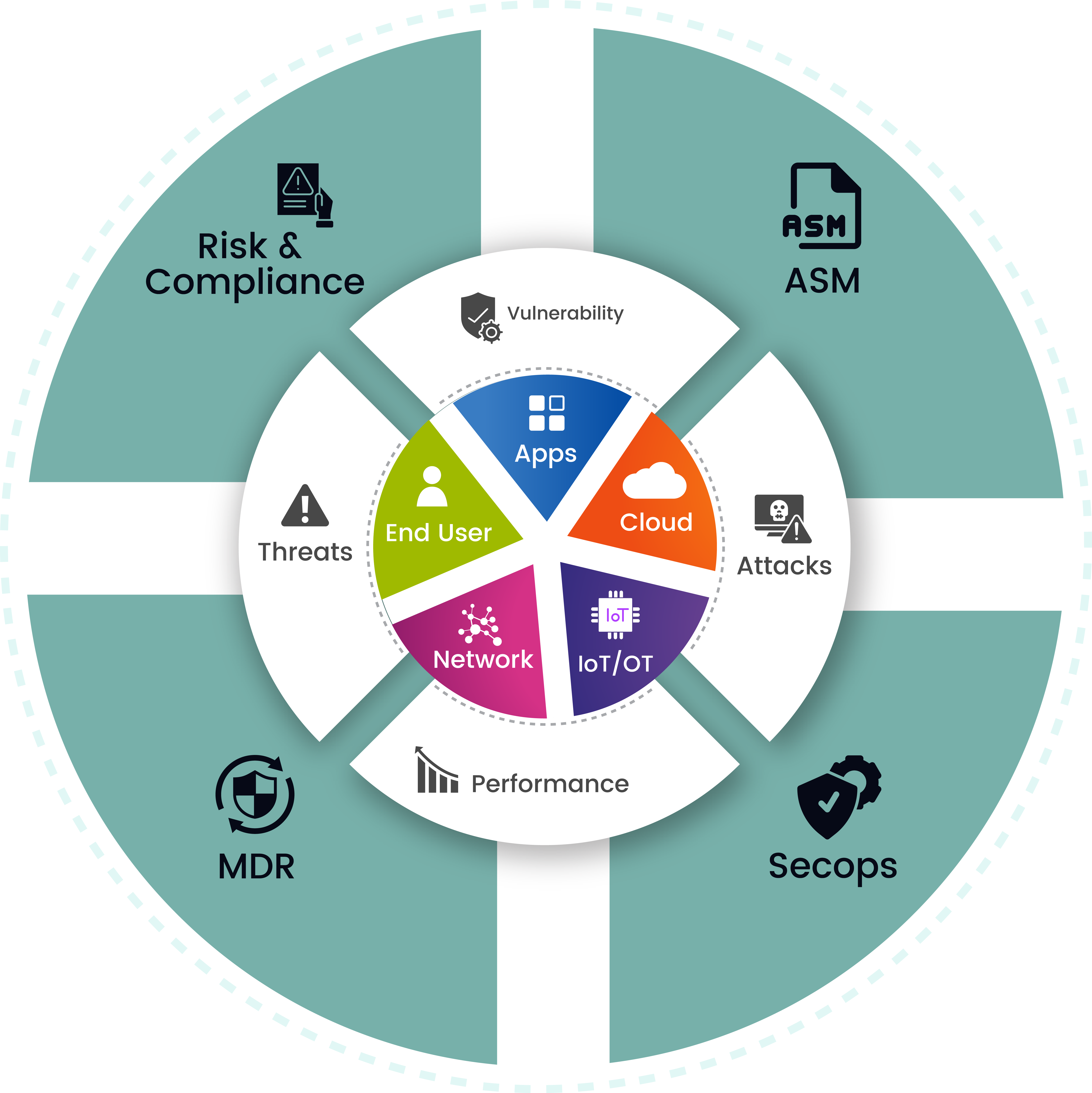
A unified cybersecurity platform built for business avenues.
Discover the platform that secures and insures.
Consolidate point solutions.
Reduce costs. Stop breaches across layers.

Experience AI-based Multilayered Cyber Protection

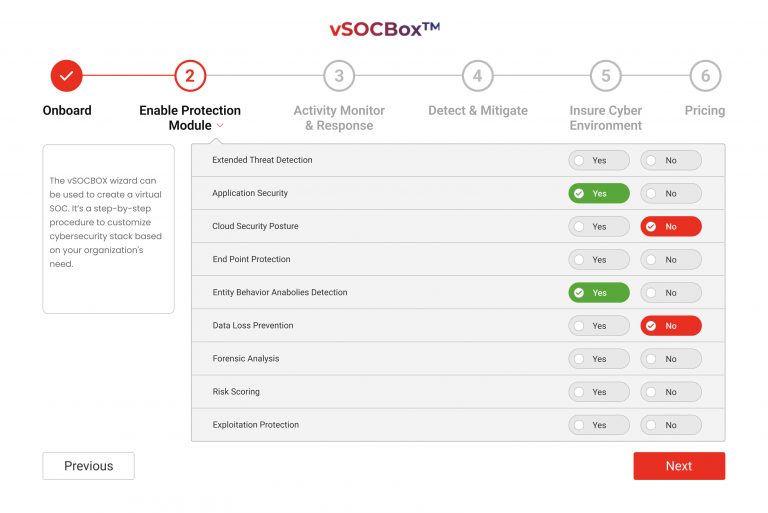
Extended Threat Protection
It is a multi-tenant architecture platform that optimizes data pipelines from different cyber-infra layers. Seamless integrations between various layers and correlation engines proactively identify all threats and attacks to remediate them in real time.

Application security
To make the apps run smoothly without any interruption, a potent cyber security solution is inevitable. Leveraging AI technology, Unified can alert system admins about the threats and mitigate them automatically.

Cloud security Posture
For seamless asset management, Unified performs log analysis, log management, and UBA. It links to cloud-based data and protects many attack routes, all the while disclosing the dangers of both deliberate and unintentional data exfiltration.
End point protection
To help organizations effectively defend against phishing attacks, strengthen resilience, and future-proof their systems, our platform integrates email, perimeter posture, browsing, and awareness culture into a single native solution.

Entity behavior anomalies detection
Our device agent was created with the ability to simultaneously identify and isolate compromised devices while keeping an eye on servers that are at risk, email attachments, downloads, and unusual activities.

Data Loss Prevention
For many firms, proprietary data is essential, and in the current world of compliance and legislation, there is always a risk of data loss. Unified links to cloud-based data and protects many attack routes while outlining the dangers of both deliberate and unintentional data leakage.
Optimum Security and Insurance
Unified Cybersecurity Platform is a one-stop solution to address all your organizational security requirements. Be it Network, Cloud, End-users, IT, IoT/OT, or Applications, this platform has it all. Through the integration of AI-based cybersecurity technology and extensive insurance knowledge, Unified presents a multi-layered platform with Threat Intelligence, VMD, Correlation Engine, and Deep Security Analytics that enables constant monitoring, data analysis, data management, threat identification, categorization, mitigation, and optimization to avert future attacks and reduce associated risks.

Real Time Protection
With a precise risk assessment and remediation strategy, it is simple and quick to activate for real-time protection of digital assets, both internal and external.

24/7 MDR
The platform involves continuous monitoring of the organization’s network to detect suspicious activities, analyze those, and take action in real time to protect it from any probable attacks.

Insure Your Business
Based on the risk score, an insurance premium is determined that is specifically customized to the needs of the business, guaranteeing the best possible cyber coverage.
We support businesses in protecting their data and digital assets with:

100+
Number of partners

125+
Clients

13500+
Total assets under monitoring

0.25 M
Critical threat detection

$ 18 M
Average financial loss prevented

$ 62.5 M
Worth cyber insurance covered
More Power to you with Multilayered-Protection on a Single Platform

SIEM & UEBA
AI\ML-Based Sim Engines: Comprising four sub-engines, included threat intelligence, VMD Engine, Correlation Engine, Deep Security Analytics and UEBA engine. These four major engines form the foundational components of our integrated solution, fortifying our capability to detect and respond to a broad spectrum of cyber threats effectively.
EDR
With the help of in-built policies, it captures the malicious activities in the registry, files, network connections, etc., and mitigates them in real-time.

Vulnerability Management Detection and Response
VSocBox identifies the weak points in the system that may be exploited by the threat like unusual services running, vulnerable open ports, weak authentication, etc., and remediate it proactively.

Log Management
This sophisticated solution establishes a centralized platform, orchestrating the efficient management of logs sourced from a diverse array of origins. This incident log is helpful for reporting, documenting, and forensic analysis as well as for maintaining regulatory compliance. Identification of anomalies.

Cloud Security
Ensure optimum protection of your assets with log management, log analysis, and UBA without affecting the accessibility.

Cyber Insurance
Stay insured from any financial damage that may incur from data breaches or cyberattacks.

Intelligent Automation
Smart automation of the SOAR platform enables center stage to automate incident reporting and remedial actions. Leveraging playbooks, the platform executes automation protocols.

Risk and Compliance
It helps an organization adhere to almost 21 security standards and regulations such as HIPAA, SOC2, ISO 27000, SEBI, etc. It establishes a strong risk-based control so that the organization can achieve compliance with CIA (Confidentiality, Integrity, and Availability).

App Security Management
Ensure uninterrupted discovery, analysis, categorization, mitigation, and monitoring to address vulnerabilities prevent potential attacks, and create a safe digital infrastructure.
How it Works?
- Getting onboarded
- Enabling the protection module
- Activity Monitoring & Response
- Detection & Mitigation
- Insuring the Cyber-environment
- Pricing
Why to create your own SOC in box?

Holistic Protection
For the organizational network, cloud storage, end-user devices, IoT/OT devices and applications, one platform is capable enough to predict, detect, remove and prevent all possible cyber attacks.

Convenient
This intuitive, next-gen platform powered by automation technology can perform the task of detecting, preventing and protecting digital assets without any intervention. Convenience at its best!

Cost Effective
Reduce the cost of installing and maintaining five different software. With one single platform, Unified Cybersecurity platform, you can secure all organizational assets together.

Futuristic
Be safe from all financial risks that come with cyber attacks, data loss, phishing, malware invasion and more. It has a futuristic solution to protect you from such financial hazards.
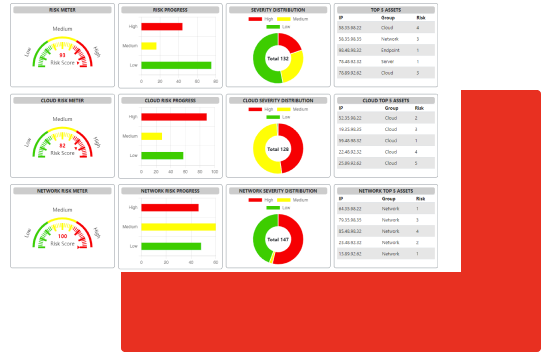
A Single Pane of Glass
Dashboards
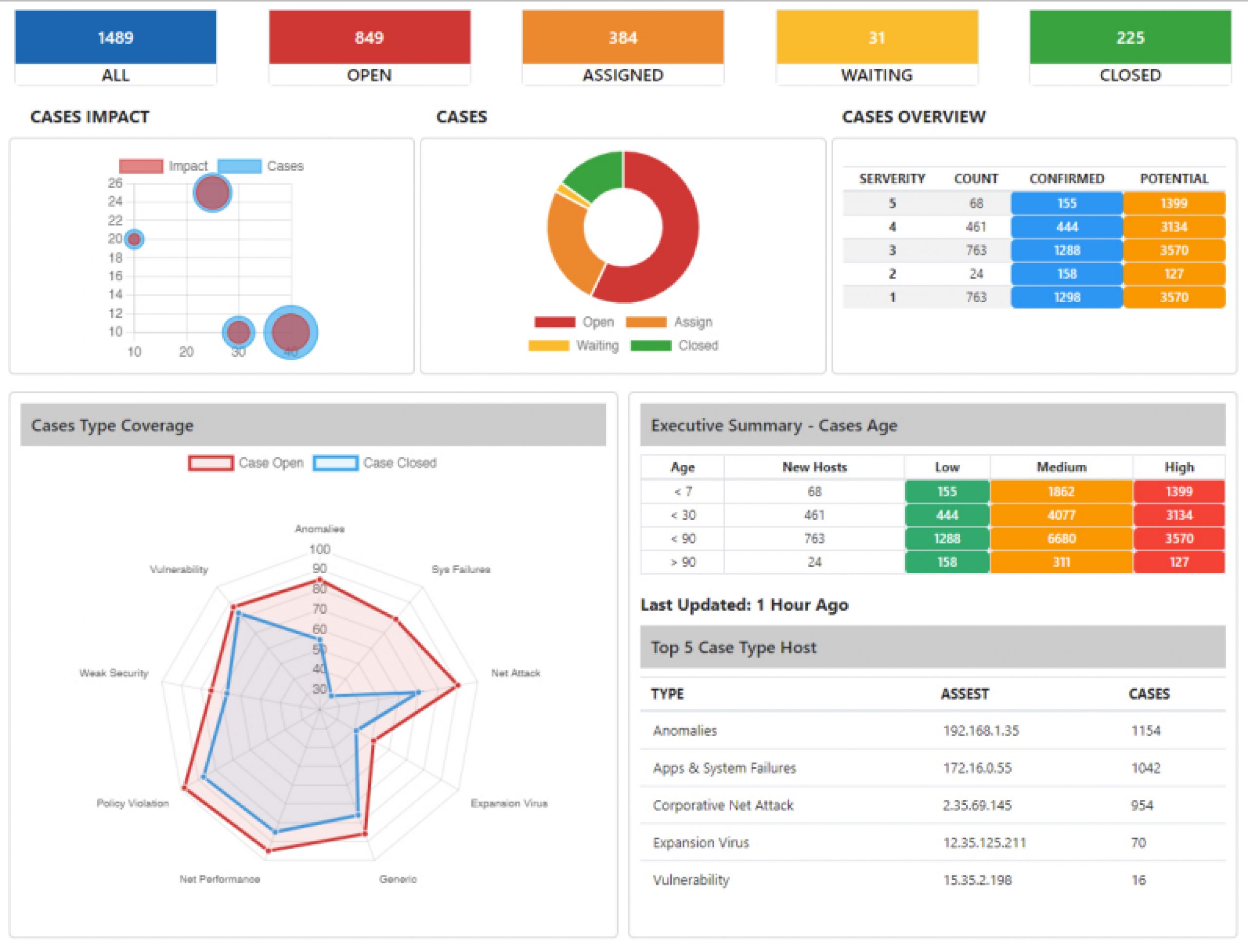
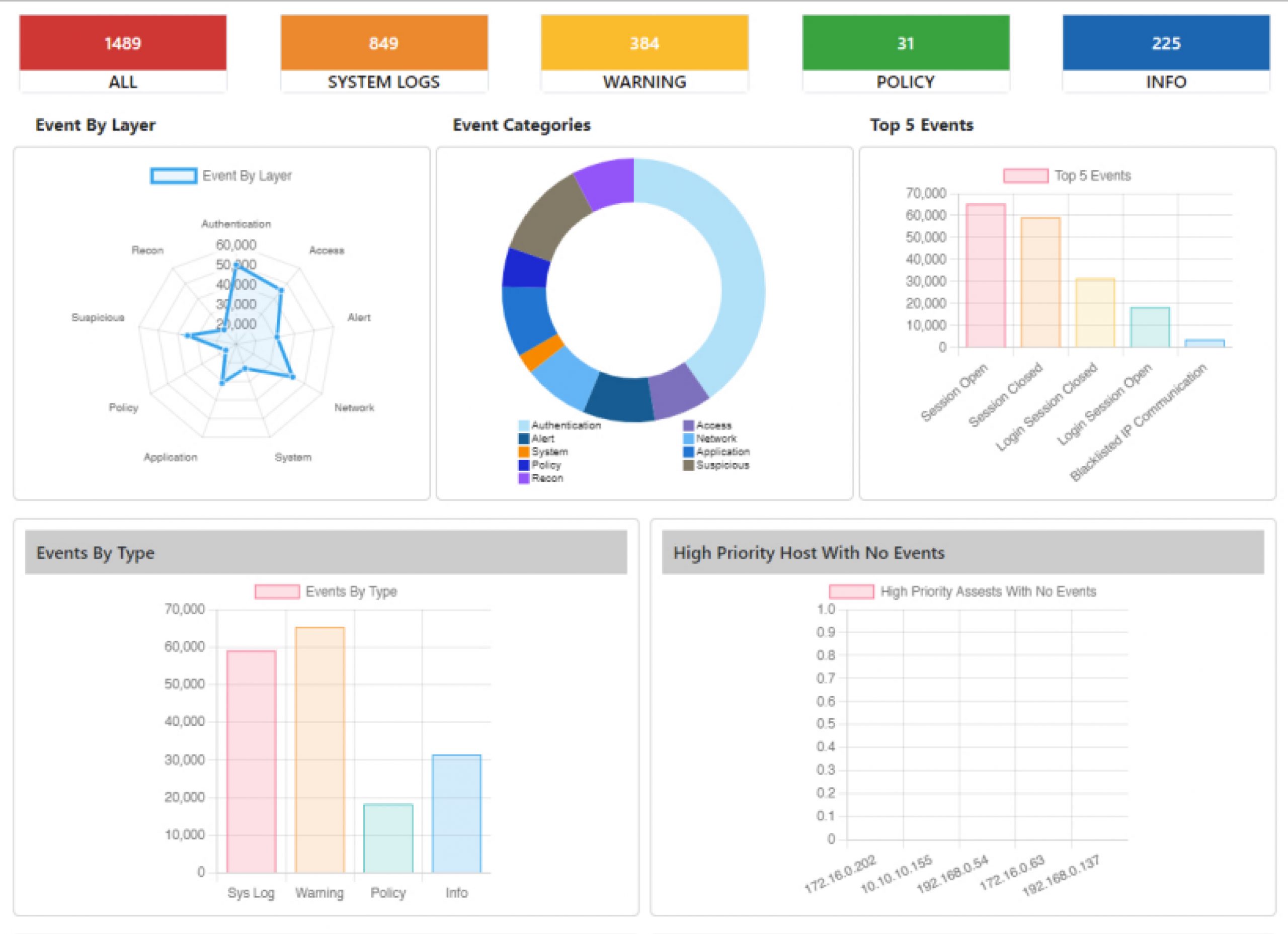
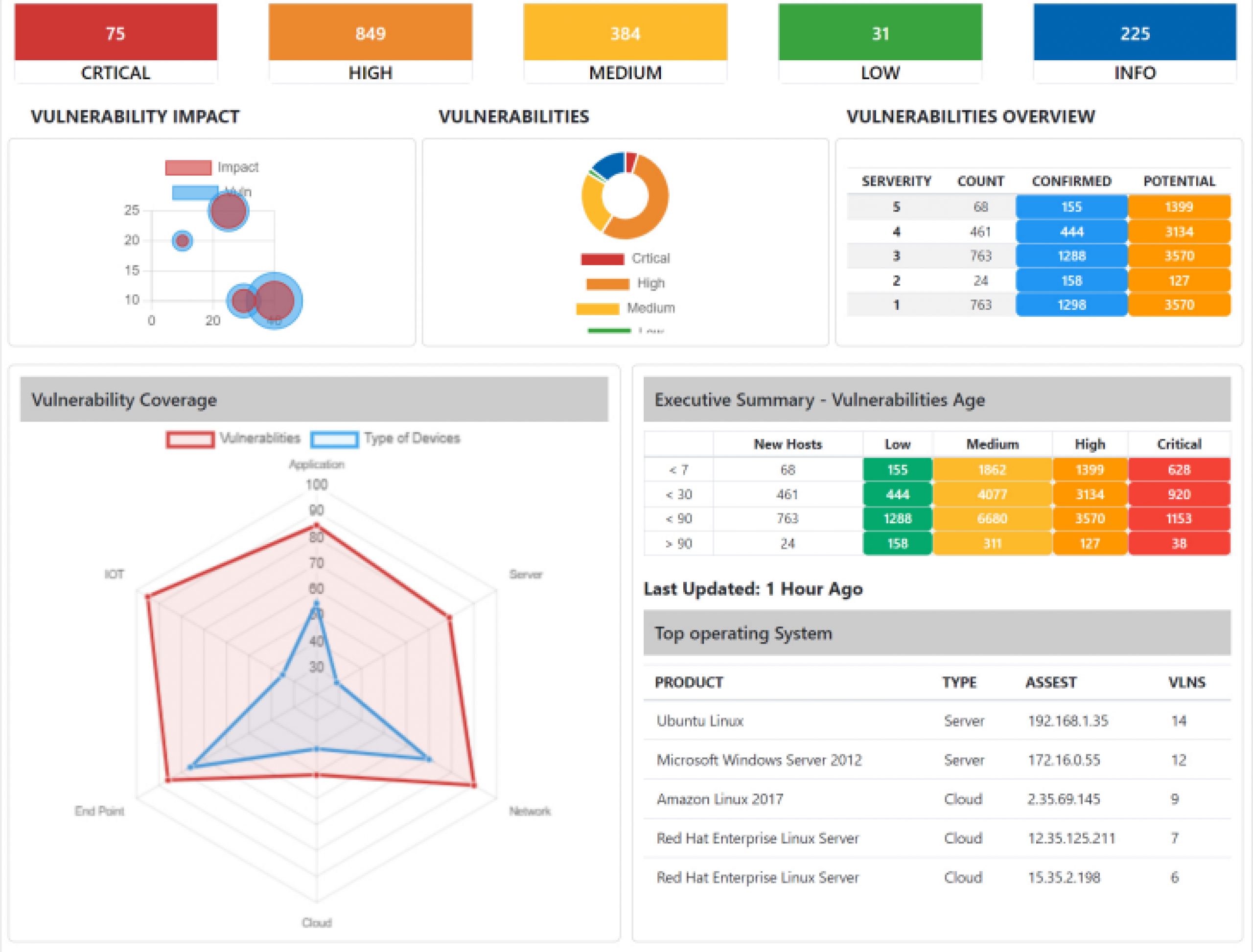
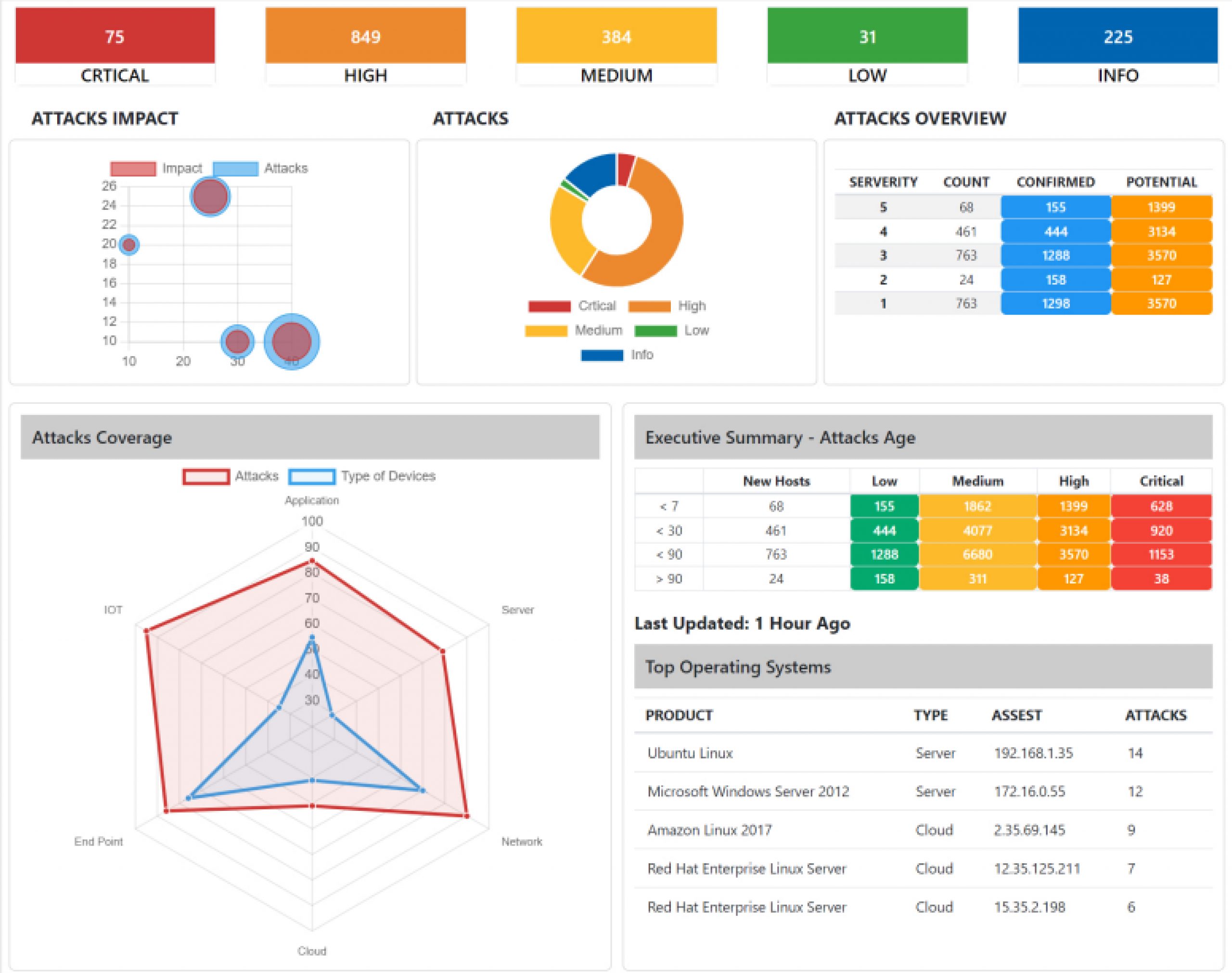
Start your virtual SOC in box
Get in Touch
Got a query? Kindly fill in the form and we shall get back to you.
We would love to hear from you.
